Strengthening Your Security Posture
Serverless Best Practices for Evolving Applications

Enterprises taking advantage of modern security practices (think moving target defense, granular least privileged access/execution of services) are moving from dedicated instances to serverless architectures. Thus, they rely on modern managed services e.g., functions-as-a-service, managed databases, API gateways, pub/sub and queueing systems, etc.
It’s the progress of security practices like this that caught my ear in this final week of re:Invent. In particular, Benjamin Smith’s talk highlighted common security challenges and how to successfully navigate them.
Smith's presentation looked at challenges associated with a growing serverless application. His insights around the “Lambda-lith”, mono-repos, and managing multiple AWS accounts are worth checking out, but in this post I summarize my favorite section of his talk around enforcing security best practices:
- Moving from castle & moat to zero trust.
- Using permission boundaries to limit the scope of a function’s execution role.
- Monitoring; keys, secrets & Parameters; and, business-approved code libraries.
Moving from castle & moat to zero trust
Smith highlighted an important shift required to modernize enterprise security—moving from a castle & moat approach to a zero trust approach. Castle & moat refers to "protecting network perimeters with firewalls, proxy servers, honeypots, and other intrusion prevention tools".
In a modern serverless architecture Smith recommends individually protecting each resource and enforcing strict verification of the users, services, and resources that can interact with each resource.
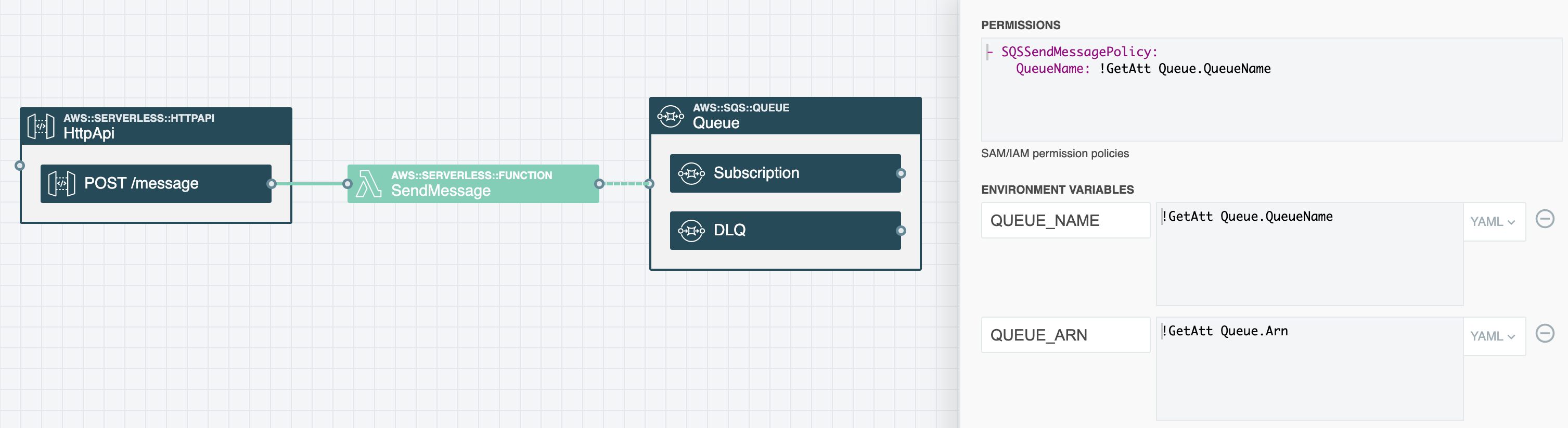
We see this show up commonly as customers use Stackery to ensure—rather than simply trying to use—least privileged access between resources.
Using permission boundaries to limit the scope of a function’s execution role
Smith then turned to looking at effective permissions: the overlap of application permission boundaries defined by an admin, with a function's execution role. This highlights how "execution permissions can be limited by the application's permission boundaries".
The slide below does a great job articulating how permission boundaries can limit functions, and importantly, how function permission that breach those boundaries are not authorized.
Monitoring; keys, secrets & Parameters; and, business-approved code libraries
AWS has a vast library of modern managed services that help companies take advantage of the latest, proven technologies—without the burden of the overhead. Smith summarized a few key capabilities that AWS provides to help ensure a strong security posture.
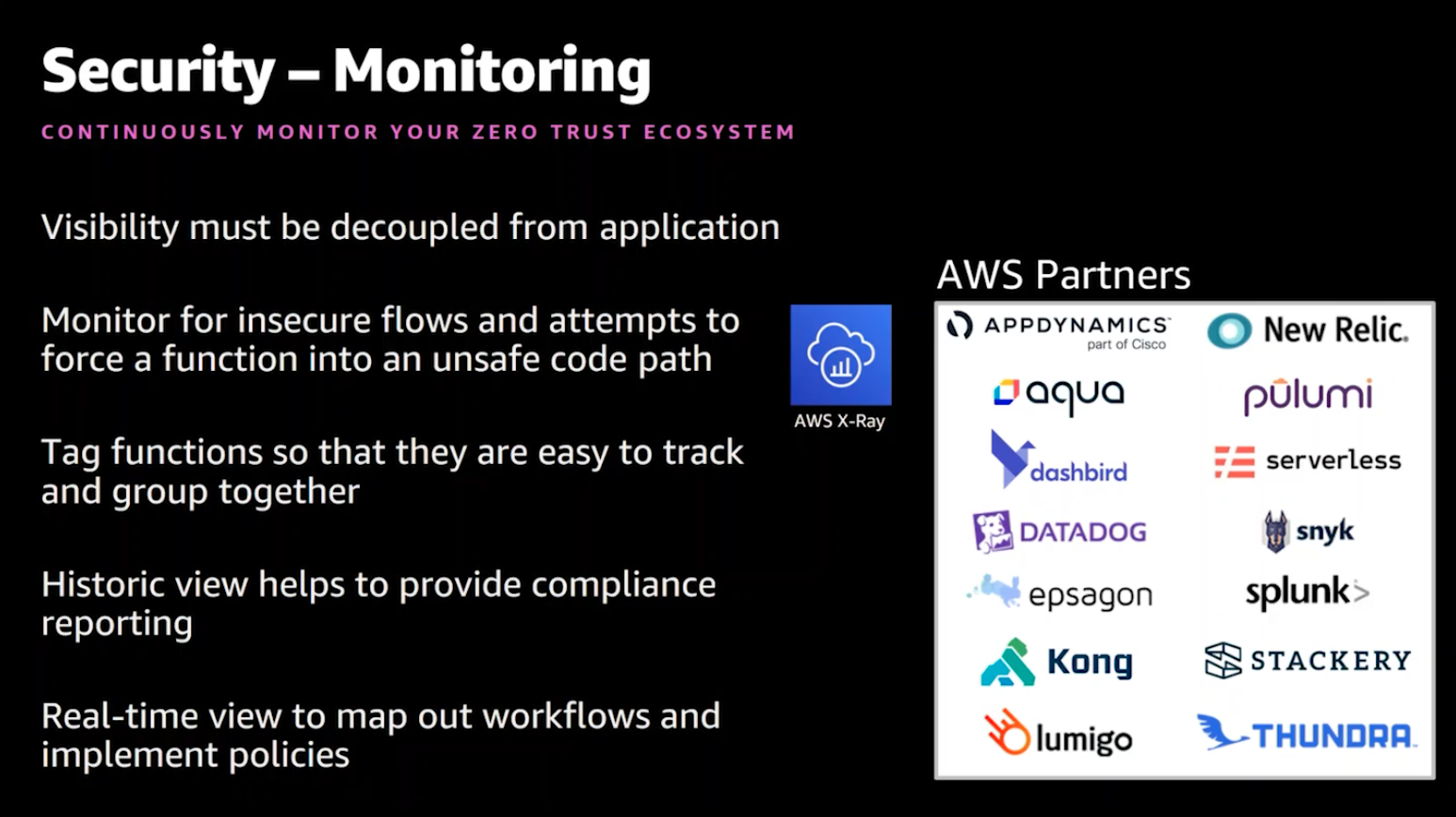
AWS and their partner ecosystem provide a host of options for continually monitoring a zero trust ecosystem.
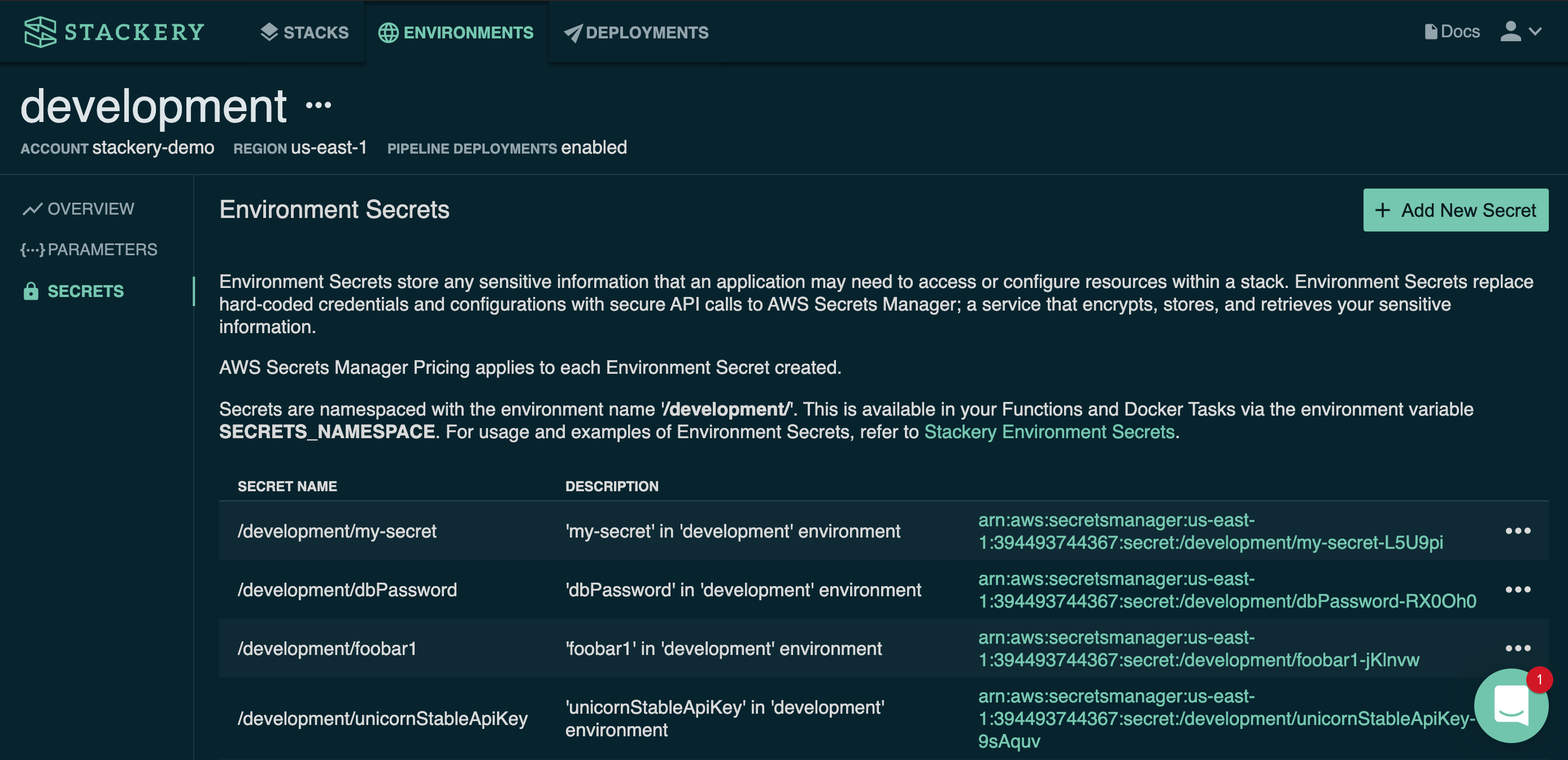
Smith touched on the importance of managing secrets and parameters, highlighting best practices that include storing secrets in order to have a single source of truth, enabling an automated and scheduled rotation, and auditing access.
Stackery helps customers with secrets and parameters, in that secrets and parameters can be abstracted from the resources and applied automatically and securely across environments.
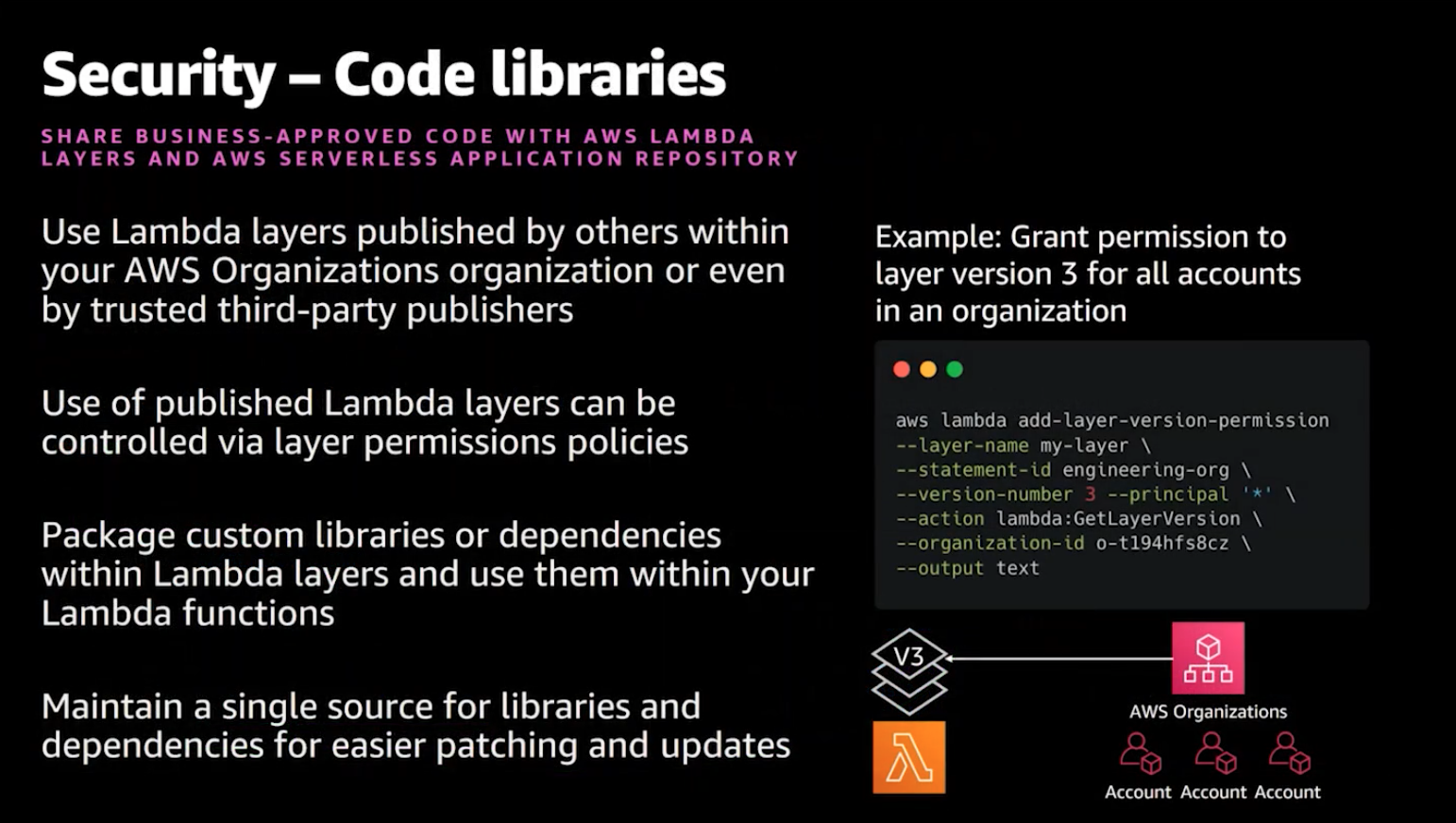
Finally, Smith discussed the value of approved code libraries. This is an emerging area that we are excited to work with AWS to further best practices that go beyond Lambda Layers.
Summary
Though serverless offloads much of the infrastructure, operational, and security concerns to your cloud provider, you still have to keep up with the latest best practices for the portions of the application and infrastructure that you do control. Smith does a great job highlighting common challenges, including how to progress your security posture to take advantage of the best of the cloud. Be sure to watch his whole session when it's available on-demand.
Related posts

Getting the developer and operator workflows right is a key success factor in the next wave of cloud adoption and innovation

Enabling Serverless in the Enterprise

And Enterprise IT gets to figure it all out …