Stackery announces the availability of Bastion modules on the CloudFormation Public Registry
Truly composable and maintainable CloudFormation is now within reach

AWS CloudFormation Modules, now available for public use through the AWS CloudFormation Public Registry, are a huge step forward for enterprise IT teams to create large manageable Infrastructure-as-Code (IaC) practices around CloudFormation. We’re excited to support the launch today with our own Bastion module. Unsure what Modules are? Read on.
Why do we need CloudFormation Modules?
Adopting managed services for your business apps, like those from AWS Serverless, empowers teams to move faster with predictable, repeatable, building blocks—from storage to streaming to compute and more. These services shift so much complexity and overhead into AWS but teams still needs to understand and operate infrastructure-as-code to employ them sustainably.
Stackery’s helped hundreds of enterprise teams solve the challenges around designing and developing architectures on top of AWS CloudFormation and AWS SAM, but for the most part folks are writing templates from scratch, for every project. This presents a challenge for teams who want to research best practices, codify those in their Infrastructure-as-Code, and expect any new teammate to pick up and run with a given pattern or blueprint.
That’s been a tough problem to solve until the introduction of AWS CloudFormation Modules. These provide a first-party means to encapsulate configuration for many AWS services into a single reusable bit of CloudFormation that can be referenced as a much simpler resource-like statement in your code.
Okay, but how do they help, really?
Your templates are suddenly more readable and maintainable.
For example, many of Stackery’s customers stamp out a Bastion-style EC2 instance to provide secure connectivity into their VPCs in order to perform operational tasks. It’s a cookie cutter pattern used all over, and it spreads out across several resources to express an AutoScaling group, IAM Roles, Security Groups, and more.
As raw CloudFormation, that’s over 200 lines of code that need to be organized, understood, and maintained over time in every stack that needs a Bastion.
Need to bump your instance size? I hope you parameterized that data. Updating security practices in your security group? Don’t forget about VS Code’s multi-file search and replace.
Honey, I shrunk the code
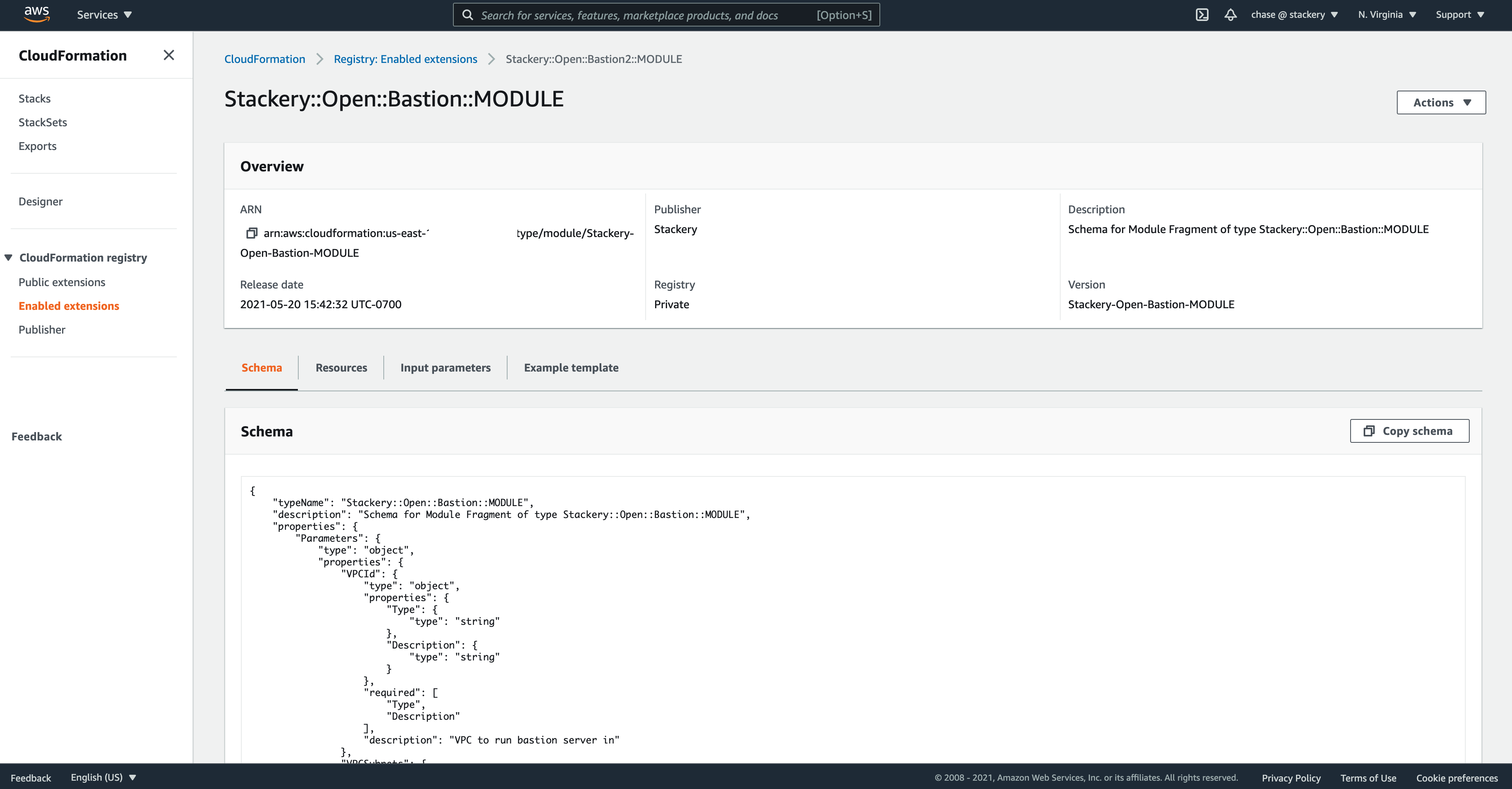
With AWS CloudFormation Modules, your organization can describe all of this in a repository dedicated to the Module, register the Module with your AWS accounts, and then use a much more coherent snippet of IaC in your application templates.
Resources:
Bastion:
Type: Stackery::Open::Bastion::MODULE
Properties:
VPCId: $VPC_ID
VPCSubnets:
- $Public_Subnet_ID_1
- $Public_Subnet_ID_2
- $Public_Subnet_ID_3
- ...
Whoa! So what’s the punchline?
You actually get to realize reusability for each critical pattern of IaC your organization is using. Further, those responsible for curating the security, cost, resiliency or other characteristics of your infrastructure only need to focus on the module repository. Consuming teams can apply versioned updates as part of their development process.
We’ve been excited about Modules since they were announced late last year but the ability to create and share both privately within the enterprise and publicly between companies truly unlocks the potential. Over time, we look forward to refactoring Stackery’s Design Canvas to promote consumption of reusable components in addition to the best-practice scaffolding our customers enjoy today.
How can I subscribe to your module?
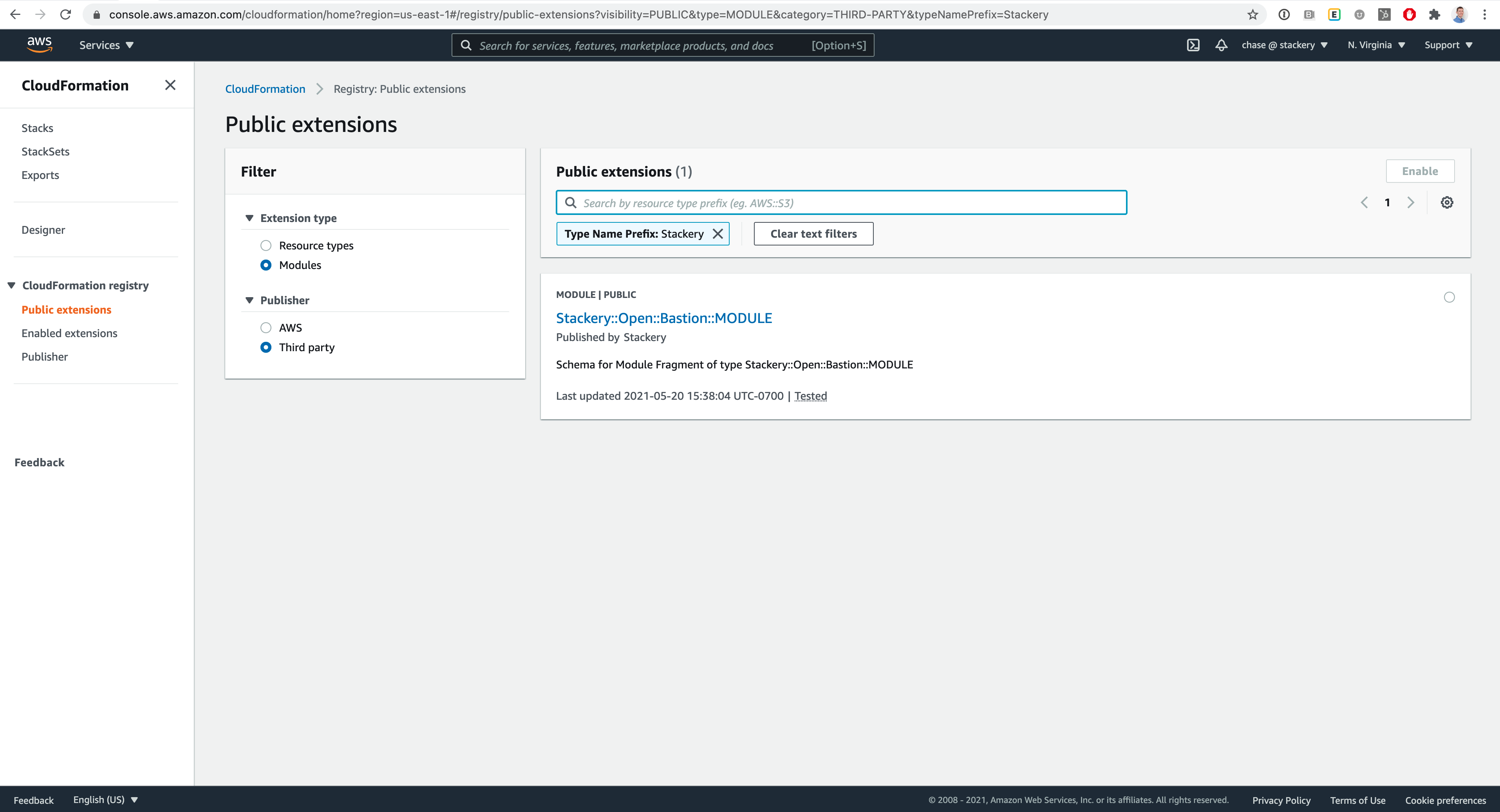
Organizations like Stackery can register as publishers on the CloudFormation Public Registry, then modules are registered with CloudFormation much like private resources or modules are today.
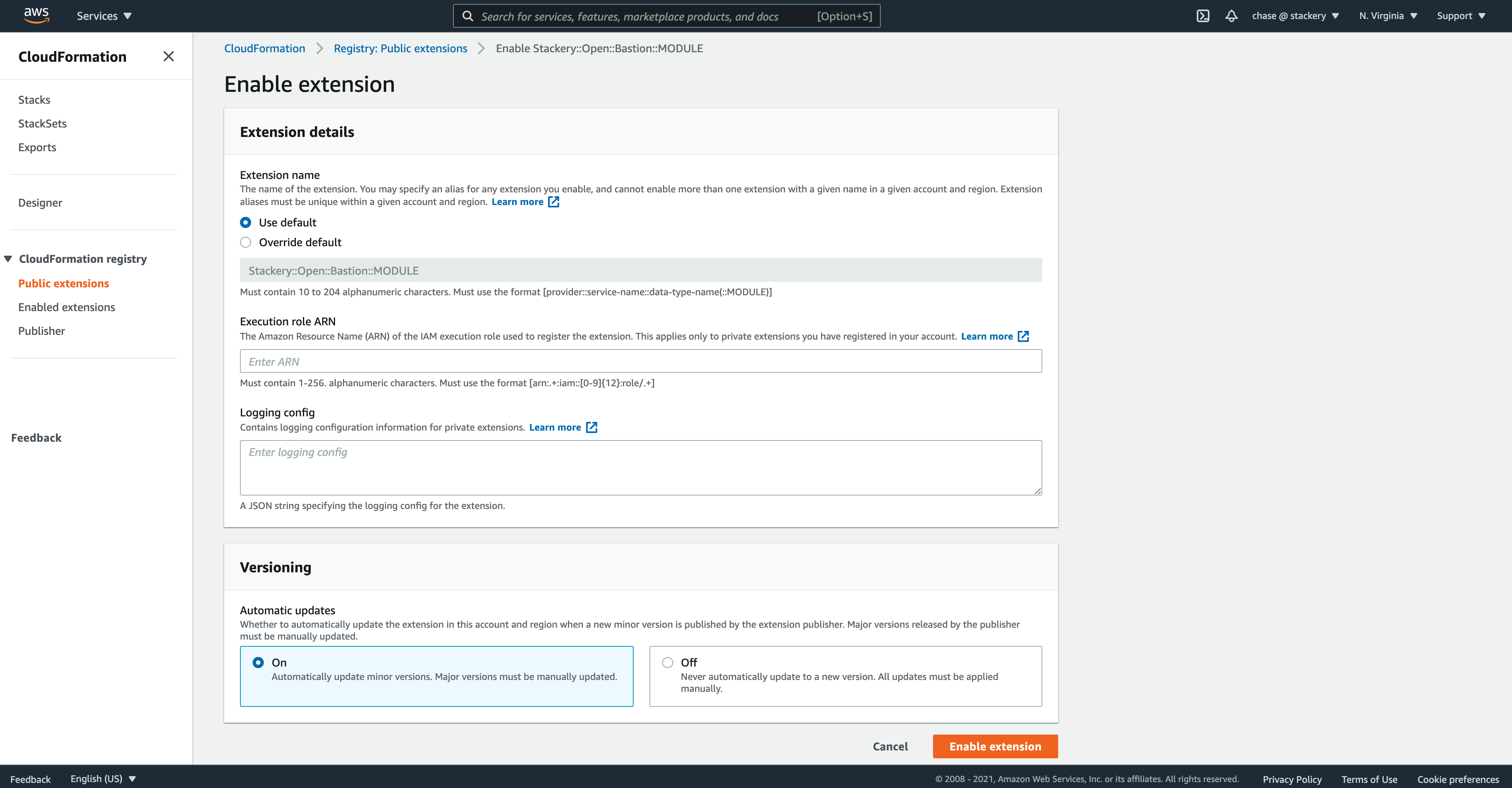
Once registered in each applicable region, public modules can be searched for, activated, and then managed with a few steps in the AWS Console. From then on, you can reference the Module in your CloudFormation templates, manage versions, and enjoy more reusable infrastructure-as-code.
Get started with your own example through the AWS Docs and share what you’re working on with us through the in-app chat!
Related posts